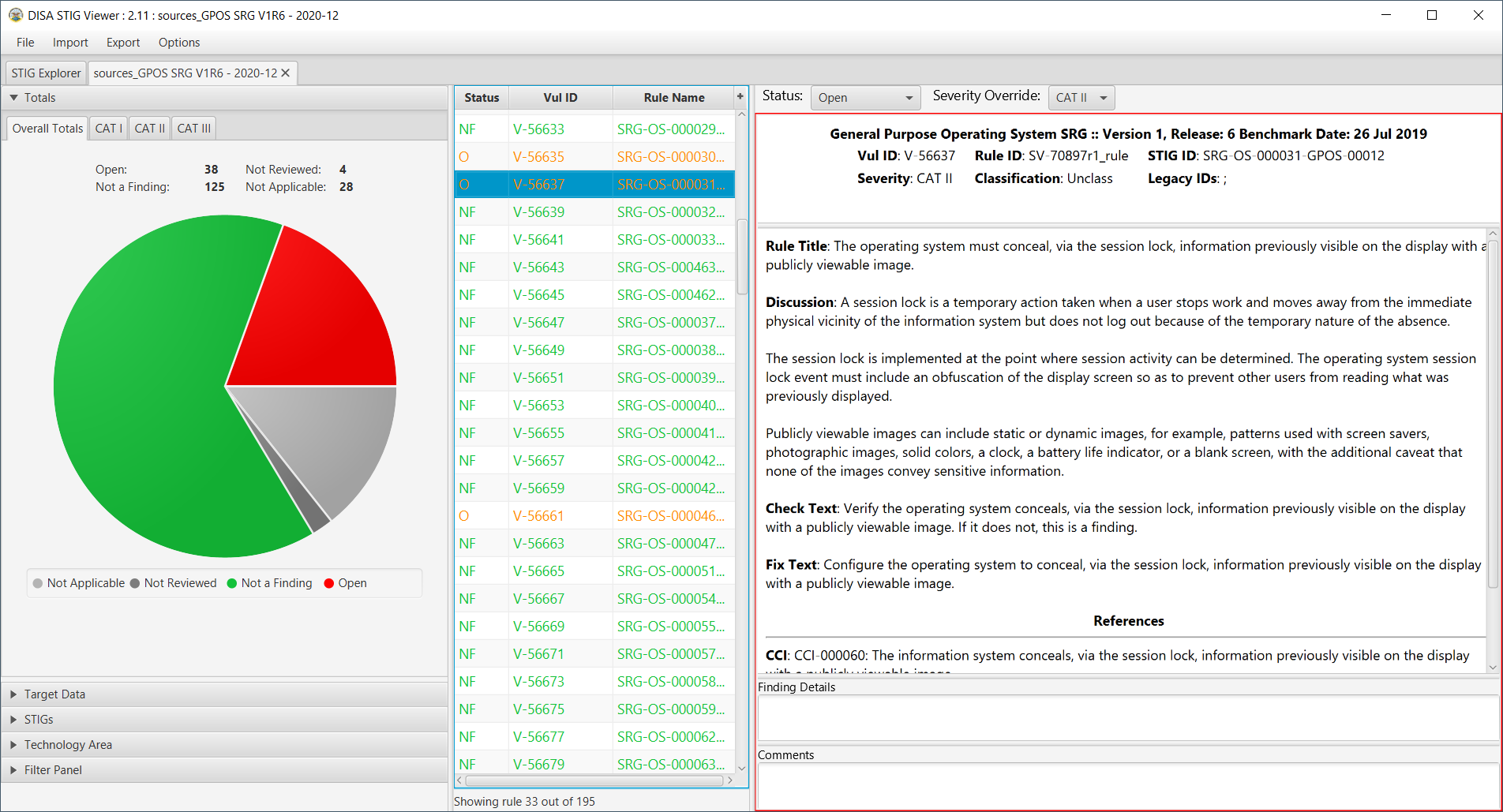
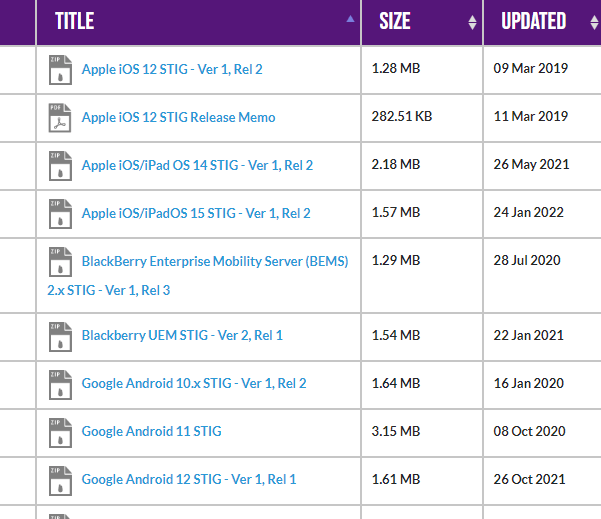
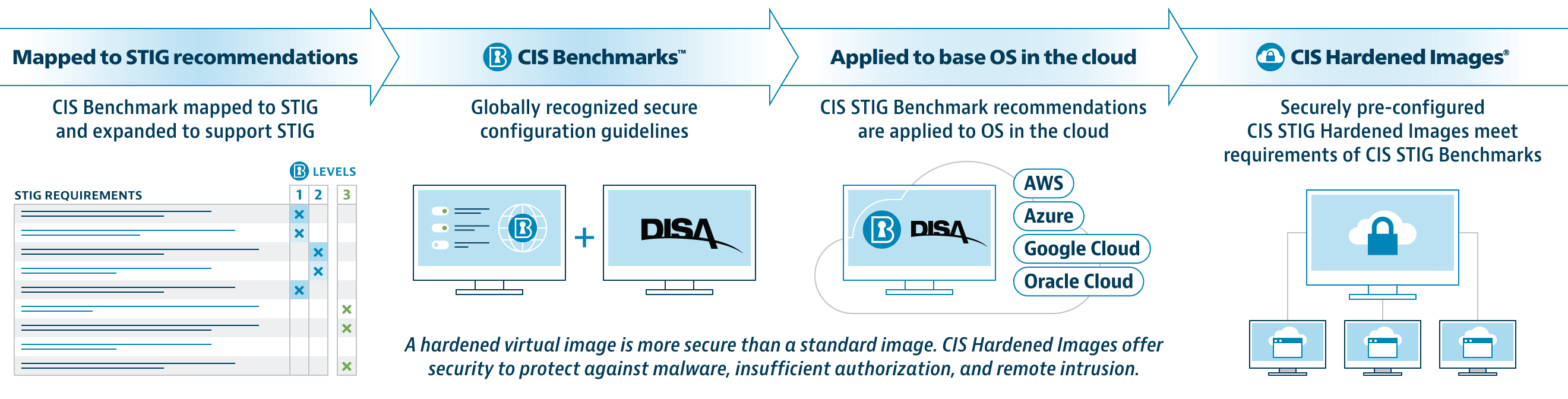
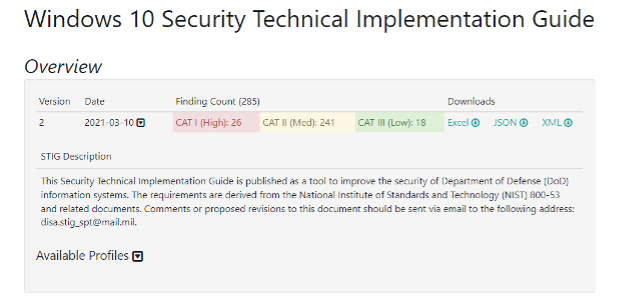
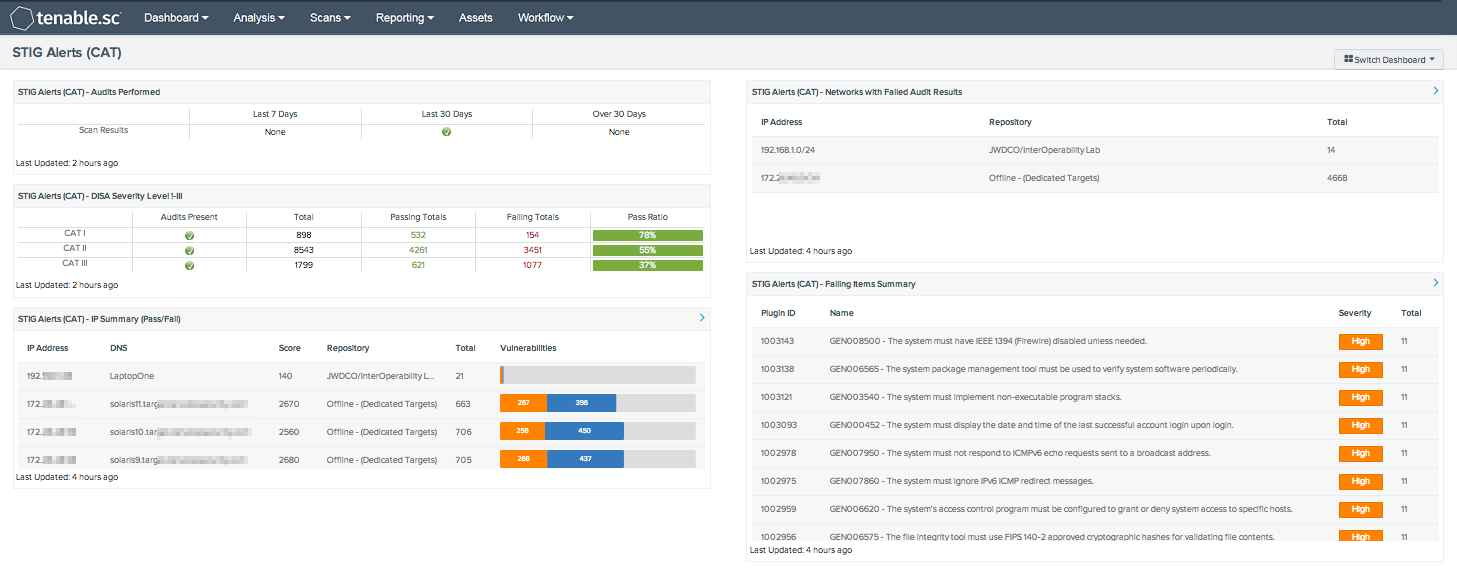
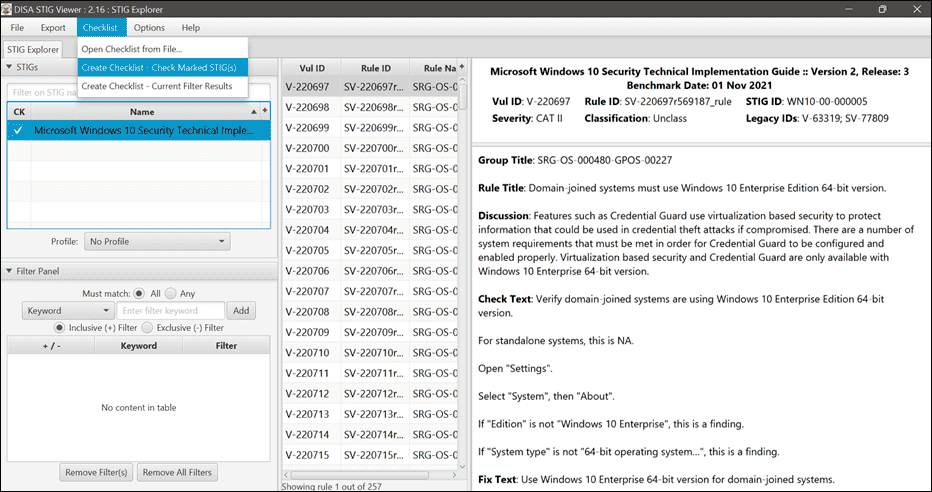
How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems
Defense Security Service Industrial Security Field Operations National Industrial Security Program (NISP) Authorization Office
GitHub - simeononsecurity/Standalone-Windows-Server-STIG-Script: Enhance the security and compliance of your standalone Windows servers with our STIG script, specifically designed to meet DoD STIG/SRG requirements and NSACyber guidance. Achieve ...
Defense Security Service Industrial Security Field Operations National Industrial Security Program (NISP) Authorization Office

How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems